Most organisations are collecting and generating exponentially increasing volumes of data each year. However, many organisations struggle to safely and efficiently dispose of data that is no longer needed for regulatory retention requirements or for legitimate purposes, as required, for example, under the Australian Privacy Principles (APPs), the General Data Protection Regulation (GDPR) and the Californian Privacy Rights Act (CPRA). On top of the complexity of keeping track of data within the organisation, the perception that data is ‘the new oil’ and increasingly cheap storage costs are typical reasons why data is not actively managed and disposed of when no longer required.
The Optus Data, Medibank and Latitude data breaches, together with the increasing number of decisions by regulators in the US and EU, underscore the risk and consequences of over-retention of data for organisations. Most of these decisions on over-retention of data arise from inadequate cyber security and have resulted in monetary sanctions and, in some instances, ongoing supervision by third parties of the organisation’s cybersecurity and information lifecycle management measures. With increasing regulatory focus on protection of personal information, organisations should be reviewing their overall information lifecycle management and specifically how they manage data collection, classification, retention and disposal to be compliant with applicable records, privacy and cybersecurity regulations and reducing risk.
What are the risks?
Failure to properly govern information assets and implement a robust data lifecycle management program will result in significant risks and costs for organisations. In a data breach, the loss of historical personal data that the organisation has no legitimate reason to be holding onto compounds the reputational damage, increases the likelihood of heavier regulatory investigations and actions, and adds fuel to the fire of any potential class actions against the organisation and directors and officers arising from the breach. Additionally, retaining unsupported legacy systems to host and manage historical data also increases the chances of a breach incident and reduces the overall security posture of the organisation.
As part of due diligence on information governance, boards and senior executives need to satisfy themselves that the organisation has an effective information lifecycle management program to manage data (and paper) from collection all the way through to secure archiving and disposal. With the volume of data being generated and collected by organisations ever increasing, this requires a collaborative and planned program carried out on an ongoing basis.
What is information lifecycle management (ILM)?
ILM is the system by which an organisation controls the collection and generation of data, storage, use and disposal of data and information. It is important to remember it also includes management of physical records, paper documents and artifacts, which continue to be generated and stored in archives either onsite or in external storage facilities.
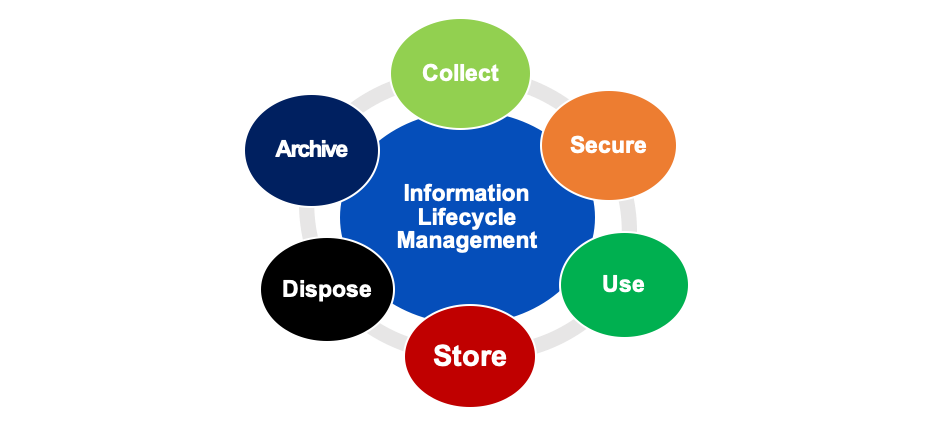
What are the benefits of information lifecycle management?
The benefits of robust ILM include:
- Improved data availability and reliable access for authorised users in their day-to-day work.
- Compliance with business requirements (i.e., policies and procedures) and legal/regulatory obligations such as record retention and disposal
- Security, auditability and custodianship of data and information are maintained, regardless of any changes in the underlying ICT infrastructure.
- Ensuring ICT infrastructure supports the business and business users to carry out their work efficiently.
- Minimising risks by reducing volume of personal data collected/retained and active disposal of information no longer required for business or legal purposes.
- Cost efficiencies through reduced storage, streamlined eDiscovery processes in legal proceedings, and decreased forensic costs in data breach investigations.
ILM Policies
Many organisations find it challenging to even initiate an ILM program, encountering significant change resistance when attempting to balance the tension between various business processes wishing to retain data (e.g. marketing and business development) and following best practices for privacy and regulatory requirements for data minimisation. It is important to ensure that all the relevant policies and processes relating to ILM across the organisation are aligned and that there is an ongoing collaborative mechanism to improve, implement and resolve issues.
IG Alignment of Policies and Procedures Diagram
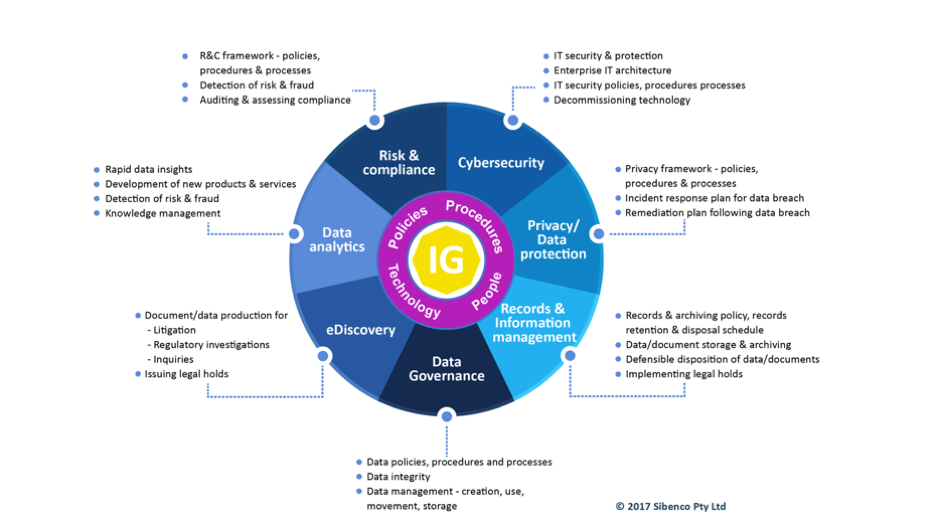
Some standard ILM policies and processes organisations should be ensuring are operating effectively and efficiently include:
- Privacy Policies and Collection Notices which inform customers about personal data that is collected, how it is used and managed, and how long it will be retained.
- Data Privacy and Information Security Impact Assessments for internal data analytics and business intelligence and for technology projects involving the use of third-party technology.
- Data Standards and Processes, which inform employees about the standards for data including, data owners, metadata, data classification and data taxonomies.
- Record Retention and Archiving, which governs retention periods of different classes of documents in accordance with regulatory and business requirements and the archiving requirements.
- Litigation Holds and eDiscovery which governs document production in litigation, legal proceedings and investigations.
- Decommission of systems, which governs the process for data removal and transfer and/or disposal of data.
- Procurement policies and processes and requirements around third-party suppliers in relation to data storage and location, information security standards of the third-party supplies and auditing of security post contract.
As can be seen from the above, ILM policies typically cover a number of different organisational areas with different types of professionals responsible for implementing and overseeing the execution of these policies. For example, the records retention and archival policy is the responsibility of the Records area, which sets the retention periods for each category and type of document in accordance with the myriad of regulatory requirements with advice from the Legal Department and the requirements of the business. All data and records collected and generated should be securely disposed of in accordance with records and retention policy.
However, the action of deletion and secure disposal of electronically stored data is usually undertaken by IT specialists. This requires the IT department to be confident in executing on disposal of data, meaning a good working relationship between Records, Legal and IT is essential to ensure that data disposal is carried out in accordance with all of the relevant policies and proceedings. A good example of how this working relationship should operate is when organisations are involved in legal proceedings or regulatory investigation. The ordinary destruction of relevant data and records is required to be halted by the placing of a ‘legal hold’. The legal hold is generally issued at the order of the Legal Department, pursuant to the Legal Hold Policy and the cessation of data and records disposal continues until the ‘legal hold’ is lifted when the proceedings have concluded. While the Legal Department is responsible for the issuing and lift of ‘legal holds’, the actual work to stop the ordinary destruction process of relevant data is the responsibility of the IT area.
Deletion rules can and should be coded into the technology systems holding the data to enable automatic deletion at an appropriate point in time. This requires appropriately skilled Records and IT personnel to set the retention and deletion rules for all the different types of data within the technology system. At the moment however, most organisations are still at the starting gate and there is very little, or no data being automatically deleted when it should be. It is far more common for data in organisations to be simply moved from primary systems to archival systems or other storage containers.
In the face of increased regulatory activity to sanction organisations that fail to have adequate systems in place to protect personal data and information, it will be increasingly important for organisations to improve on the status quo. Implementation of effective ILM policies and processes along with appropriate oversight mechanisms through robust Information Governance to ensure ongoing best practice is essential for the effective management of data and information.
ILM – where to start?
The starting point is to identify any gaps in the organisation’s policies and procedures and then to ensure that all the relevant policies and processes are aligned under the overarching Information Governance policy and framework. Alignment of policies and processes across the organisation is key to ensuring that everyone within the organisation from the board and senior executives down to each user within the organisation is both able to understand and comply their obligations to protect the organisation’s data and manage it in accordance the policies and procedures.
A collaborative mechanism to improve, implement and resolve issues is necessary. Ideally, this should be the Information Governance Committee, which can provide oversight on the adequacy and compliance of all policies and procedures relevant to the overarching Information Governance framework, which includes ILM. Where gaps are identified, the Information Governance Committee should ensure that adequate action is taken to remedy the gap on an ongoing basis.
The role of Information Governance and ILM
Information Governance provides an overarching mechanism for boards and governing authorities of organisations to control and effectively manage enterprise-wide information assets so that value is maximised and risk is reduced to acceptable levels. As the diagram below illustrates, there are many different parts of the organisation with different drivers around data and information, including ILM.
For example, innovation, AI and use of innovative technologies may lead to personal data being over collected and stored on an ongoing basis. Retention and use of this data, particularly if it is personal or sensitive in nature, needs to be balanced against the risks of ensuring compliance with changing and growing privacy regulations. This example would also require consideration of ethical use of AI in light of reputational issues that may arise.
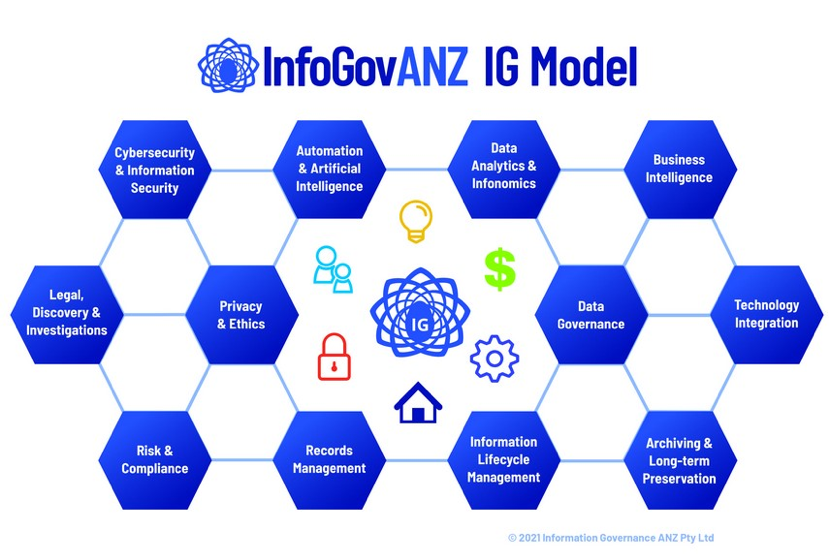
The InfoGovANZ Model highlights that while different areas across the organisational silos are responsible for different aspects data, information and technology, effective governance will ensure they are also co-ordinated and aligned so that overarching organisational objectives can be achieved. ILM is a core part of the overall Information Governance model, sitting along the bottom row as a foundation element along with records management, archiving and long-term preservation and risk and compliance.
Traditionally, record retention and archiving has been the responsibility of Records and Information Managers who traditionally reported to the General Counsel, and in many organisations continue to do so. However, the modern reliance on IT systems to carry out the execution of ILM policies have skewed responsibilities increasingly towards the IT Department. Regardless of where responsibility resides, these processes need to be co-ordinated between records, legal and IT. Where organisations are not actively managing their information lifecycle, implementation of these processes will require substantial effort to overcome change resistance and bring departments together. It often will require further investment in upskilling of staff to both understand and given them confidence to actively manage data through its lifecycle and across the organisational silos.
A robust information governance framework implemented from the top-down and an overarching Information Governance Steering Committee are key factors which can help organisations to implement and drive ongoing ILM.
Read more here in the Information Governance Primer
Author: Susan Bennett, LLM(Hons), MBA, FGIA, CIPP/E Founder of InfoGovANZ, Governance and Privacy Lawyer